- Home » News » World News
Knowledge base will help to prepare for ICS cyber-attacks

A US organisation has compiled a knowledge base of the techniques that cyber-criminals use when attacking industrial control systems (ICSs). The impacts from these attacks can range from disrupting operations to harming human life and the environment.
The ATT&CK for ICS database has been created by the Mitre Corporation – a non-profit company that operates federally-funded r&d centres and public-private partnerships in the US, aimed at tackling problems that challenge safety, stability and well-being.
The ICS knowledge base describes the actions that adversaries might take when operating in ICS networks. It is intended to characterise and describe their behaviour after compromising an ICS installation, helping potential targets to prepare better for such attacks.
Mitre suggests that the knowledge base could play several roles for defenders, including helping to establish a standard language for reporting incidents. It could also be used to develop ways of responding to incidents, prioritise defences and find gaps, report threats, train analysts and emulate adversaries during exercises.
“Asset owners and defenders want deep knowledge of the tradecraft and technology that adversaries use in affecting ICS to help inform their defences,” says Otis Alexander, an engineer who focuses on ICS cybersecurity at Mitre. “Adversaries may try to interrupt critical service delivery by disrupting industrial processes. They may also try to cause physical damage to equipment. With Mitre ATT&CK for ICS, we can help mitigate the catastrophic failures that affect property or human life.”
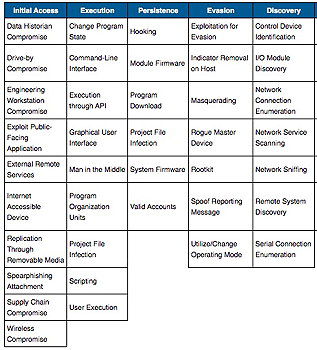
More than 100 participants from 39 private and public organisations contributed to the database before its launch. They included cyber-intelligence and security companies that focus on ICS, manufacturers, national labs, research institutes, universities and government agencies.
Austin Scott, principal ICS security analyst at Dragos, says that the new database “shines a light into the unique threat behaviours leveraged by adversaries targeting ICS environments. It is a huge win for the front-line ICS network defenders who now have a common lexicon for categorising ICS-specific techniques to support reporting and further analysis”.





